10 Benefits of Custom Software for Your Business – Fewer Resources, Greater Efficiency
Dedicated software is an investment that increases company efficiency, minimizing IT resource consumption and supporting a sustainable development strategy.
 Author:
Author:Join us for a continuation of our discussion about the Rubber Ducky device, its homemade alternatives, and ways to defend your company against such attacks. If you’re not familiar with how BadUSB works, we encourage you to read our previous post.
Low-cost alternatives to Rubber Ducky
Due to the high price of the USB Rubber Ducky, also known as BadUSB, many alternatives offering similar functions at much lower prices have appeared on the market. These solutions often require some programming skills or even the soldering of different types of boards to achieve a similar effect to the commercial product. The cheapest solution that enables such functionality is a solution from Digispark – a miniature module with an ATtiny85 microcontroller with 8KB of internal memory.
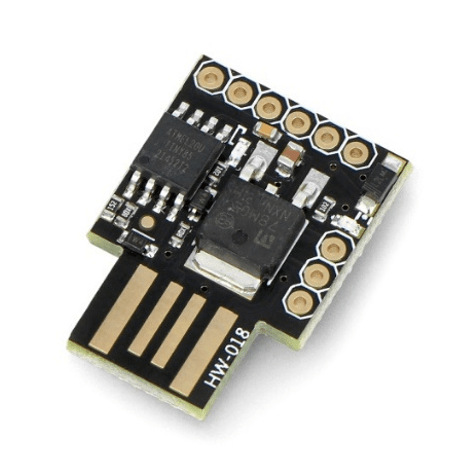
Photo 1: Digispark ATtiny85
Programming the board is very simple and is done using the DigiKeyboard library. The downside of this solution is that the board needs to be reprogrammed using software from the Arduino company every time we want a different script, and that it is necessary to wrap scripts found on the internet in commands from the DigiKeyboard library. The advantage, however, is the price, as the board can be ordered for as little as $4 from a certain Chinese website. In Poland, it costs about 30 PLN. It is worth noting that the library itself also takes up some memory, so only about 4KB is available. This may not seem like a lot, but it is enough for one script. Sample code for scripts wrapped in the DigiKeyboard library can be found here:
https://github.com/MTK911/Attiny85.
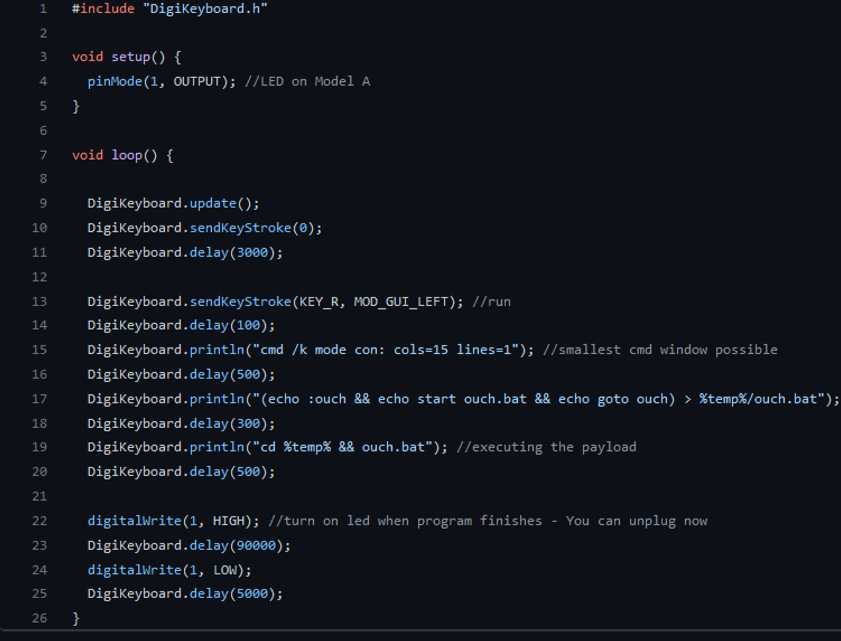
Photo 2: Github, MTK911 / Attiny85, Script DigiSpark Fork Bomb
Internet reviews, however, suggest that the DigiSpark board can be problematic and may not always be easily detected on every operating system (or even on a specific USB port). So it may be difficult to reprogram or, worse, inserting it into the victim’s computer may not trigger the script. Another solution worth discussing is the Arduino ATmega32U4 board, which can be equipped with a microSD module and switches. The whole setup, when connected and soldered, can look like this:
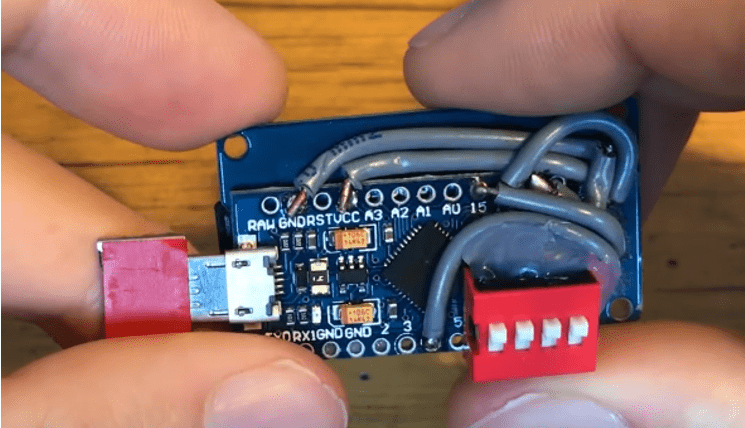
Photo 3: BadUSB created with Arduino ATmega32U4, Seytonic Youtube
Proper programming of the board enables the storage of scripts on a microSD card and their switching using soldered switches. Another advantage of this solution is the one-time programming of the board and the number of attacks that can be carried out by connecting the board only once. Script exchange is done by placing them on the microSD card using a computer or phone, while also remembering to name them properly. This is an advantage even over some of the purchased products in this area. However, the disadvantage is that such a device stands out, unlike commercial ones. Placing such a homemade BadUSB in a visible place in a company, we cannot expect someone simply picking it up and plugging it into their computer. In the case of commercial, elegant solutions, there is a non-zero probability that the victim will connect such a “pendrive” – even out of curiosity to see what is on it. The code for the solution is also quite simple, but it involves loading the appropriate “txt” file and then processing the script written in the ducky language into the appropriate commands in the C programming language using the Keyboard.h library. https://github.com/Seytonic/Duckduino-microSD
Danger at every step?
The cost of such a device varies depending on the type, manufacturer, and range of capabilities offered, ranging from $40 to $70 per unit. There are also more expensive options that hide such a device, for example in a cable, a computer lamp, or a keyboard. Therefore, it is good practice to buy devices from trusted brands and reliable sources, and not to connect unverified devices to a computer that stores sensitive data. There have been cases where criminals or legally employed pentesters have provided companies with gadgets equipped with additional, dangerous electronics and taken control of the company (or, in milder cases, simply demonstrated the imperfection of procedures).
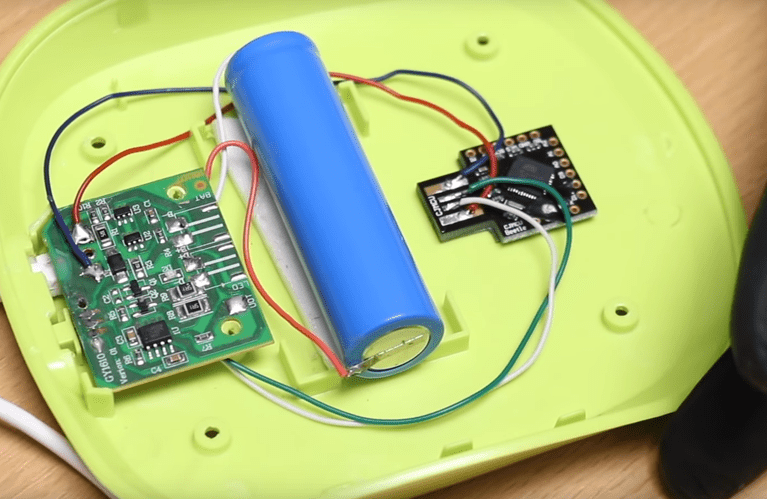
Photo 4: Digispark board placed in USB lamp, Z-Security Youtube
The official website offering original USB Rubber Ducky devices also offers cables with BadUSB functionality for $120 (OMG Cable).

Photo 5: Malicious BadUSB cable manufactured by HAK5
It should be added that there are also special detectors that control and (often, though not always) detect the presence of malicious gadgets. As with any field related to cybersecurity, there is an atmosphere of constant competition between solutions that enhance security and those that break newly created security methods.
USBKiller
It is also worth mentioning that attacks using Rubber Ducky are not the only type of attacks via the USB interface, as there are also devices called USBKillers. When such a device is inserted into a port, it begins to send signals of high voltage to damage the hardware of the targeted device. However, what will happen to the attacked equipment depends on its construction. It does not always have to damage the motherboard of the device, sometimes, due to hardware protections, faults will be limited to the USB port that is broken. In the topic of USBKillers, there is also a kind of rivalry between people striving to increase user security and those trying to break these protections.
How to protect your company?
One of the weakest links in cybersecurity is the human factor, that negatively affects the level of a company’s security. Due to the complexity of technology, threats cannot be completely eliminated, but they can be minimized. In the case of BadUSB, employee education seems to be the most important, so they don’t connect unknown USB devices. They should hand them over to the administrator, who will then verify their origin in an isolated environment. However, Rubber Ducky USB is not the only attack vector on companies. If you want to know more, we encourage you to read our blog. If you want to protect your company from cyber threats, consider hiring a specialist.
Sources:

10 Benefits of Custom Software for Your Business – Fewer Resources, Greater Efficiency
Dedicated software is an investment that increases company efficiency, minimizing IT resource consumption and supporting a sustainable development strategy.
Green IT

Responsible Software Development: How to Reduce Your Application’s Carbon Footprint?
Practical tips on how developers can actively reduce CO2 emissions by optimizing code, infrastructure, and application architecture.
Green ITInnovation

Green IT: How Technology Can Support Environmental Protection?
An introduction to the idea of Green IT – a strategy that combines technology with care for the planet.
Green ITInnovation