Green transition as the key to long-term success
Sustainability as a strategic business advantage. Why long-term thinking opens the door to greater competitiveness and new markets.
 Author:
Author:Today we want to tell you more about passwords and, most importantly, the attacks on passwords that await Internet users and programmers. Concepts related to hashes will also appear, so if you haven’t read our previous article about hashing functions on our blog, we encourage you to do so. And now, we invite you to read!
Some time ago in an article on the blog, we discussed authentication methods and identity-related issues for users. Passwords are one of the fundamental authentication methods, where users prove that they are who they claim to be. The entire process is based on the assumption that only the specific user knows the password (kept secret) and that the password isn’t easily guessable. Long ago, when good practices for creating passwords didn’t exist, people used single words, names, birthdates of loved ones, or simple numbers. Today, with the advancement of password-cracking techniques and increased computational power available, we know that such approaches are insufficient.
The answer is – it depends. It’s often said that passwords shouldn’t be encrypted and should be hashed instead. However, there are situations where applications do encrypt passwords, such as in password managers, where they must be stored as text rather than hashes. For example, the documentation for the 1Password manager states that their application uses AES-GCM-256 for encrypting passwords. In most cases, though, web applications should store passwords in the form of hashes rather than encrypting them.
If a user creates an account in our application, the application should create the account by entering the appropriate database entry. The password the user chooses should be passed to a hash function, and the resulting fixed-length string should be stored together with the account entry in the database. Other mechanisms, such as “salt and pepper,” can be added to our application, but let’s focus on the basics for now.
If a user already has an account and tries to log in to the application, the application takes the password provided, hashes it again, and checks the entry in the database. If everything matches, the application grants the user access to their account (via SessionId or Token, for example).”
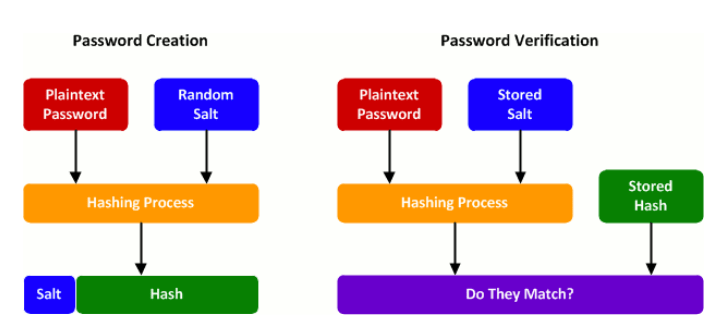
Figure 1 – Password Creation and Verification Process, Source: lucidoutsourcing
Hashing, as we remember, is a one-way mathematical function, meaning that the password cannot be retrieved from the resulting hash. This means that even if the database is breached, the hacker won’t be able to recover the stored passwords – of course, provided that we use secure practices and correctly implement mechanisms.
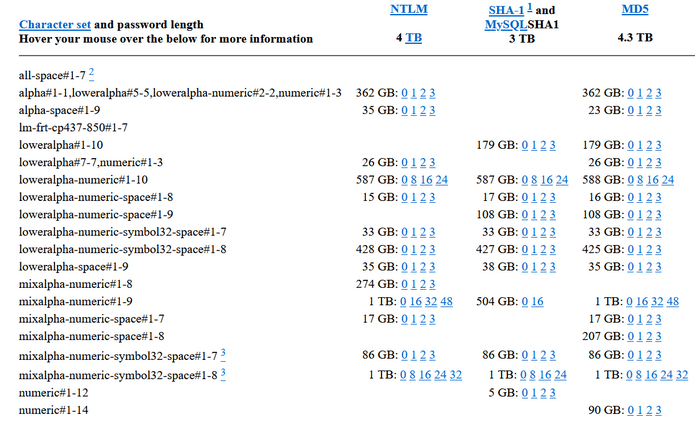
Figure 2 – Rainbow Tables for Different Password Policies and Hashing Algorithms. It’s evident that these databases often weigh hundreds of gigabytes and do not include combinations with special characters (only alphanumeric/lower alpha or numeric).”
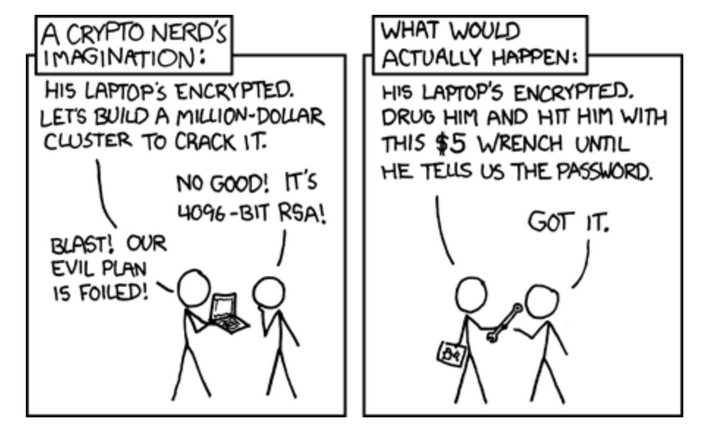
Figure 3 – Comic illustrating how, despite advanced technological security measures, overlooking physical threats can have disastrous consequences for security, Source: XKCD’s Wrench Attack Cartoon
Summary
There are numerous types of attacks, varying in technicality. If you want your company to be secure, it’s best to entrust security tasks to experts. The topic is quite extensive, but what you can do is read our articles about good cybersecurity practices to significantly reduce the chances of becoming a victim of an attack.
Next week, we will discuss good practices related to passwords – managing and storing them. Stay tuned!”
Sources:

Green transition as the key to long-term success
Sustainability as a strategic business advantage. Why long-term thinking opens the door to greater competitiveness and new markets.
Green IT

AI for a Better Future: Our Highlights from CEATEC Japan
First hours at CEATEC Official. This was my first time beeing in Japan. I expected lots of noise and tech overload. Instead, nothing but calm faces, precise conversations, quiet determination. Here, innovation doesn’t try to impress. It tries to endure. There’s something very Japanese in that: patience before progress. I’m here with INNOKREA, but […]
AIEventsInnovation

INNOKREA at EDAG Smart Industry Summit, Fulda 2025 – and what an event that was!
Promising beginnings Already on our way to Fulda, we were in high spirits😊, as if everything was going to go our way. The plane was super punctual, we got our luggage after a few minutes of waiting as the first passengers, and we rented a car from our supplier at Frankfurt Airport without any […]
AIEventsInnovation