Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
 Author:
Author:Hello! Today, as Innokrea, we want to tell you how to ensure product security within the DevOps process, what SAST, DAST, and SCA are, and how they can contribute to improving security. We also recommend our articles on IaC (Infrastructure as Code), Docker, and SDLC.
SDLC (Software Development Lifecycle) is a model that describes how the entire software development process should proceed—from planning to testing, deployment, and maintenance. However, traditional approaches to SDLC often lack explicit consideration of security as an integral part of the process. As a result, the security department may be perceived by developers as an obstacle to the rapid delivery of new features. Consequently, application security may be overlooked or treated as a secondary concern. The solution to this is an extended version of the SDLC process: SSDLC (Secure Software Development Lifecycle).
SSDLC integrates security practices at every stage of the software lifecycle, emphasizing collaboration between development, DevOps, and security teams. This ensures that security becomes part of the culture of software creation rather than an obstacle to its development.
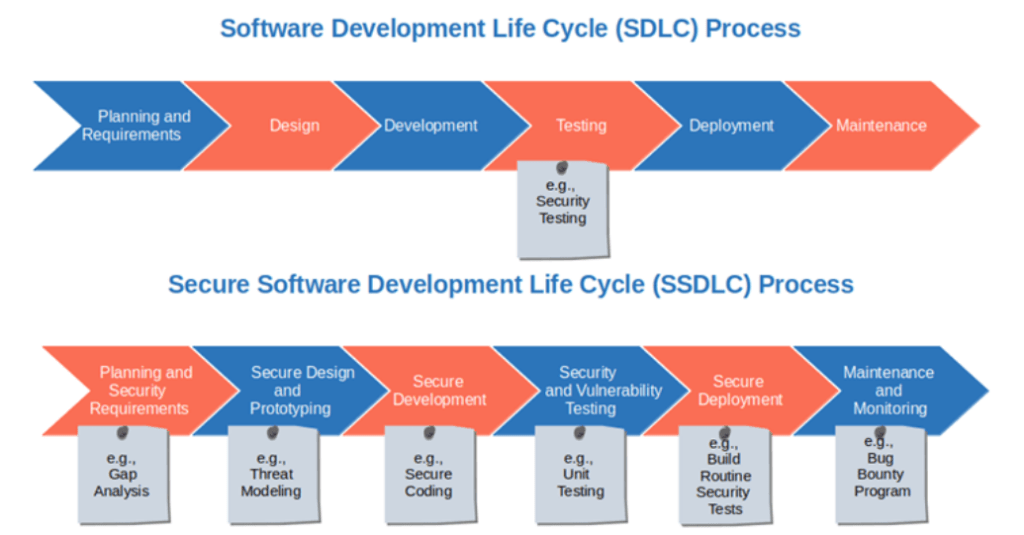
Figure 1 – SDLC vs SSDLC, source: medium.com
The stages of the Secure Software Development Lifecycle (SSDLC) can be described as follows:
The SSDLC process is often managed by a DevSecOps team—a DevOps team augmented with security expertise.
Modern applications often consist of dozens or even hundreds of components, including code dependencies and external tools. This significantly increases the attack surface and complicates security management. In the example diagram below (Figure 2), we can see numerous components involved in managing an application within the Azure cloud environment. These include:
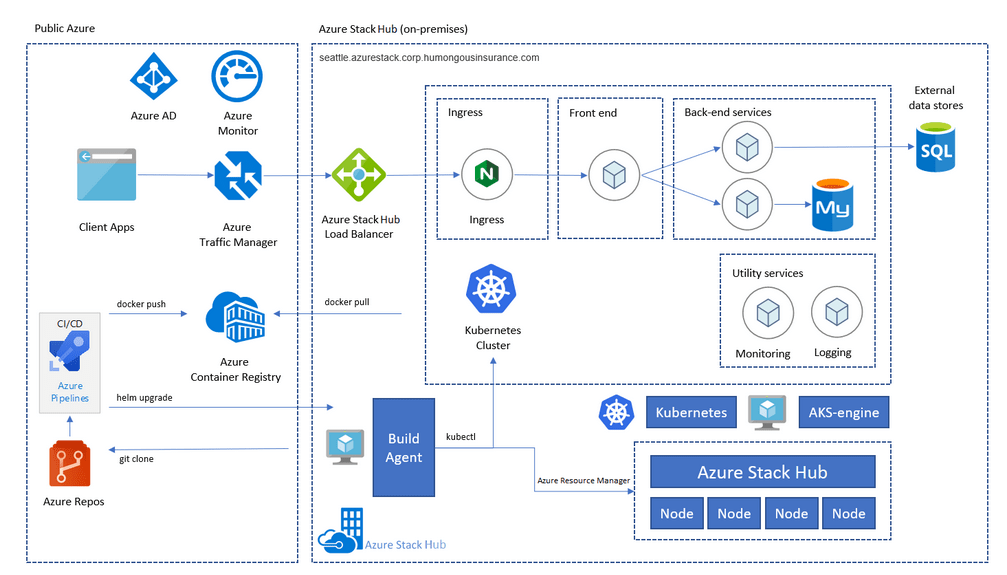
Figure 2 – Application Architecture Built on Azure Cloud, Source: Microsoft.com
In this article, we’ve discussed SSDLC and the complexities of managing application security due to the sheer number of tools and dependencies in the code. The DevSecOps approach emphasizes addressing security issues as early as possible using the so-called shift-left approach, which integrates testing—especially security testing—into the earliest stages of software development.
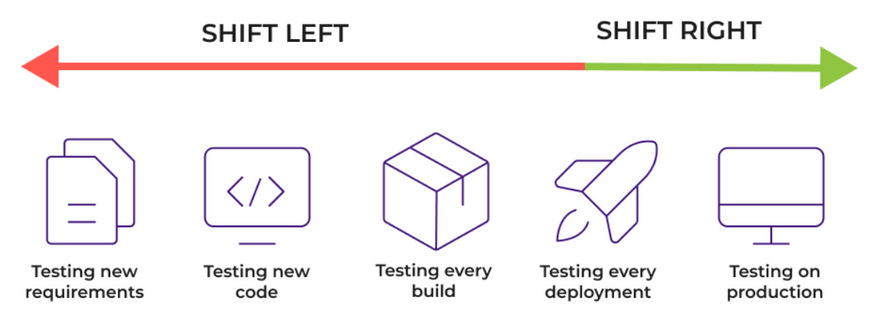
Figure 3 – Shift-Left Approach, Source: Medium.com
DevSecOps teams utilize various tools to tackle security issues across different stages of the software development lifecycle. These tools include:
These tools are often integrated into a unified solution, connected to vulnerability databases. The algorithms evaluate the severity of vulnerabilities, assess potential risks, and prioritize threats for DevSecOps teams or developers to address.
Many tools cater to some or most of the aforementioned challenges. Examples include Dependabot, Snyk, Mend, Semgrep, Fortify, SonarQube, CodeQL, Copilot, and ZAP. While we won’t describe all of them here, let’s highlight how some of these functionalities can be used in specific tools. Such tools are often employed in CI/CD processes to build pipelines for automated testing and application deployment. This ensures the process remains predictable and repeatable.
For example, the well-known juice-shop cybersecurity project provides pre-configured pipelines in GitHub Actions integrated with tools like CodeQL (static analysis), Dependabot (dependency analysis), and ZAP.
Similar ready-made configurations are available for other CI/CD tools using security solutions like Snyk and Semgrep, with scan results delivered to the respective platform for further analysis.
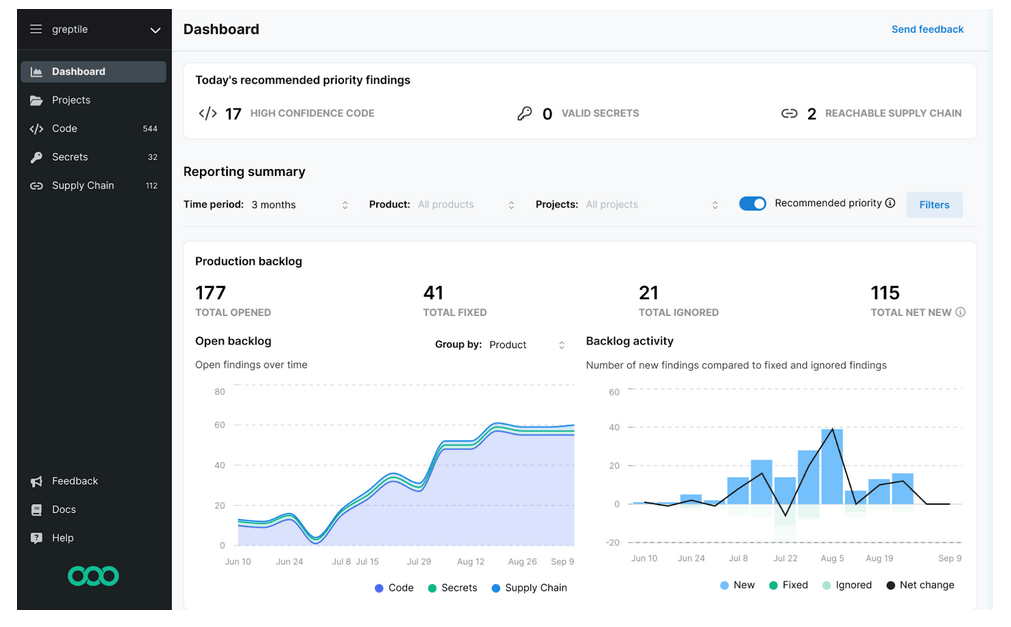
Figure 4 – Screenshot of the Semgrep Console, Source: Semgrep.dev
The implementation of plugins for scanning in the development environment can appear as shown in the screenshot below.
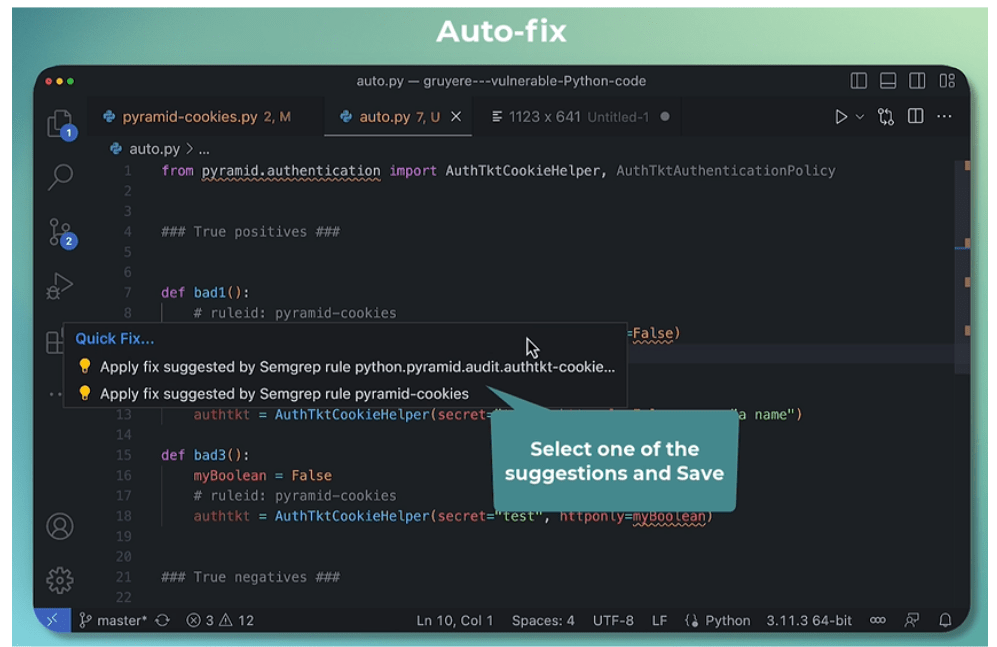
Figure 5 – Automatic Code Fixing Application via Semgrep Extension for Visual Studio Code, Source: Semgrep.dev
We hope this article has provided insight into the process of managing security from a DevSecOps perspective. DevSecOps teams integrate security into every stage of the software development process, enabling the detection and mitigation of vulnerabilities from the earliest stages of development (shift-left). With tools like SAST, DAST, SCA, and secret scanning, teams can effectively protect applications against modern threats. The SSDLC approach and automation through CI/CD pipelines ensure the consistency and repeatability of the entire security management process. For more technical details, feel free to explore the provided references.
https://medium.com/@usamayaseen/application-security-in-ssdlc-a778205ac810

Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
Green IT

Helm for the Second Time – Versioning and Rollbacks for Your Application
We describe how to perform an update and rollback in Helm, how to flexibly overwrite values, and discover what templates are and how they work.
AdministrationInnovation

Helm – How to Simplify Kubernetes Management?
It's worth knowing! What is Helm, how to use it, and how does it make using a Kubernetes cluster easier?
AdministrationInnovation