Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
 Author:
Author:Today we will tell you about how the number of devices on the Internet is rapidly increasing, and also how the number of sensors we use directly or indirectly as humans is growing. If you’re curious, we invite you to read on!
IoT (Internet of Things) is a network of embedded devices and software that together create a system for collecting and processing data from certain sensors. Examples of such devices can range from a kettle or other household appliance connected to Wi-Fi and communicating with the cloud to systems that manage, for example, field irrigation based on data collected on soil temperature or humidity. The number of applications for IoT devices is enormous, and that’s why their global count increases by several or even tens of percentage points year by year, as evident in the analysis below.
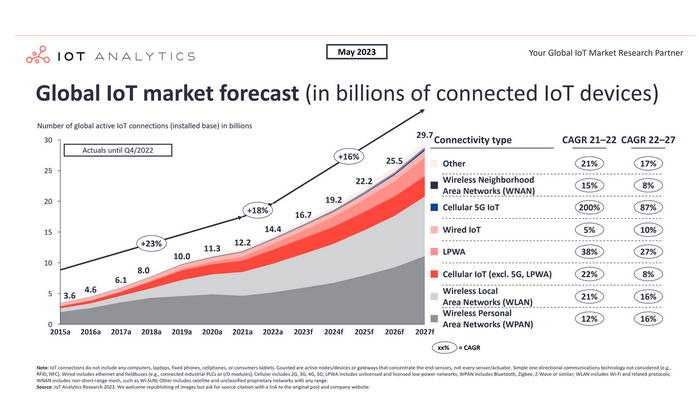
Figure 1 – Growth of the number of devices in the IoT market, source: IoT Analytics
However, few people know that the history of miniature devices began in 1982 at Carnegie Mellon University, where programmers decided to collect data from a Coca-Cola vending machine concerning the temperature and the availability of beverages.

Figure 2: Coca-Cola Vending Machine at Carnegie Mellon University, source: ops.gov.ie
A few years later, scientific work by individuals such as Mark Weiser emerged, helping to form a concept of what an IoT (Internet of Things) system could look like (one such work is referenced in the source).
In 2023, it is safe to say that the IoT market has matured, with many proven technologies available in both software and hardware aspects. IoT devices are characterized by features such as self-configuration, network connectivity, scalability (including horizontal scalability), and cost efficiency. The current state of the market has been influenced by advancements in various fields, including software engineering (algorithms for energy-saving in devices), 3D printing (for creating appropriate packaging), miniaturization of embedded devices and enhancements in their capabilities, the introduction of cloud technologies, and the increase in battery capacity and durability. It is also significant that we can incorporate multiple inexpensive sensors into devices, such as temperature sensors, smoke detectors, or GPS transmitters for tracking devices. The combination of these technologies drives dynamic market growth, enabling us to gather a vast amount of data, which, as we know from previous articles, is one of the essential elements for creating an effective artificial intelligence model.
The IoT market, like any other IT market, faces various challenges, including:
IoT systems vary depending on their application domain and their source company. In recent years, systems that leverage cloud computing for processing vast amounts of data from IoT systems have gained significant popularity.
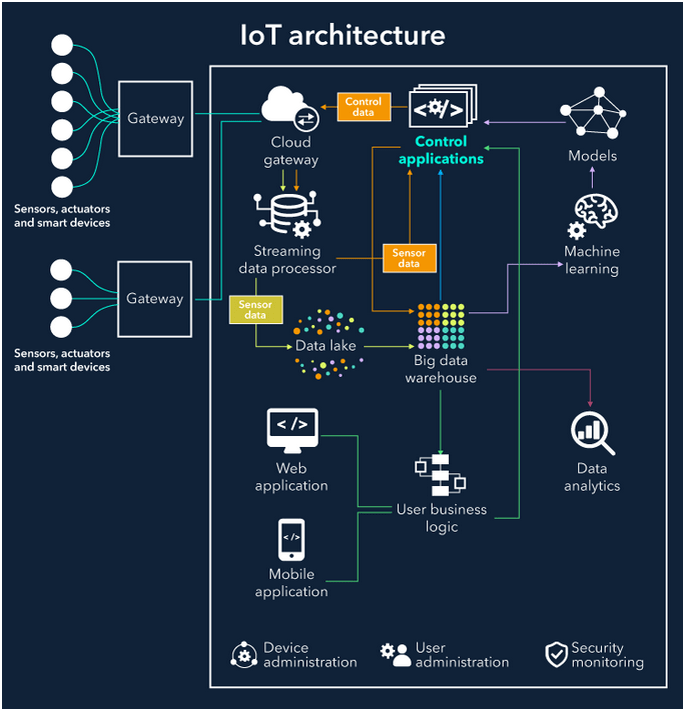
Figure 3 – IoT architecture, source: scnsoft.com
The above graphic can give us some insight into what a modern IoT system looks like. Here, we can see sensors collecting data, data aggregators, machine learning algorithms, and OLAP processing in an analytical database. The insights from processing can then be presented through a web or mobile application. Designing and implementing such a system requires expertise in a wide range of fields, from the specific business domain for which the IoT system is applied to knowledge in areas such as embedded systems, web/mobile development, analytical processing, cybersecurity, and artificial intelligence.
We hope we’ve piqued your interest for more information about IoT systems. We will continue next week, delving into the more technical aspects of IoT. If you’re interested, we encourage you to follow our blog.
Sources:

Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
Green IT

Helm for the Second Time – Versioning and Rollbacks for Your Application
We describe how to perform an update and rollback in Helm, how to flexibly overwrite values, and discover what templates are and how they work.
AdministrationInnovation

Helm – How to Simplify Kubernetes Management?
It's worth knowing! What is Helm, how to use it, and how does it make using a Kubernetes cluster easier?
AdministrationInnovation