10 Benefits of Custom Software for Your Business – Fewer Resources, Greater Efficiency
Dedicated software is an investment that increases company efficiency, minimizing IT resource consumption and supporting a sustainable development strategy.
 Author:
Author:Today we want to continue the topic of IoT for you. Today, we will talk about the more technical aspects of how IoT devices work, the protocol stacks, and the challenges that engineers have to overcome. If you’re curious, we invite you to read on!
Computer networks are built in a layered manner and are presented based on a specific network model, such as OSI. Dividing various responsibilities, such as IP addresses or port numbers, into different layers allows protocols to be developed independently of each other. This, in turn, allows different organizations to focus on different issues at each layer. The two most well-known models are the OSI reference model, which precisely divides various protocols into layers, and the TCP/IP model that operates on today’s Internet, which is a simplification of the OSI model.
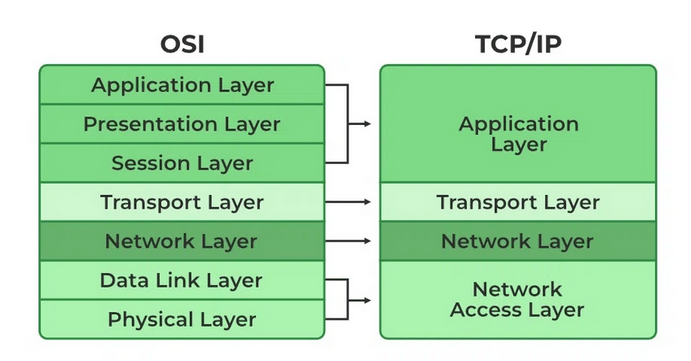
Figure 1 – Comparison of OSI and TCP/IP models, source: geeksforgeeks.com
Answering this question requires us to point out that IoT devices operate within networks and must transport data to systems that aggregate them. Additionally, in the previous post, we mentioned the diversity of technologies used to deliver data in the initial stages of communication (e.g., the communication between a sensor and a local data aggregation system). The most significant elements that differentiate standard computer communication with the Internet from IoT device communication are the protocols found in the application layer and the data link layer.
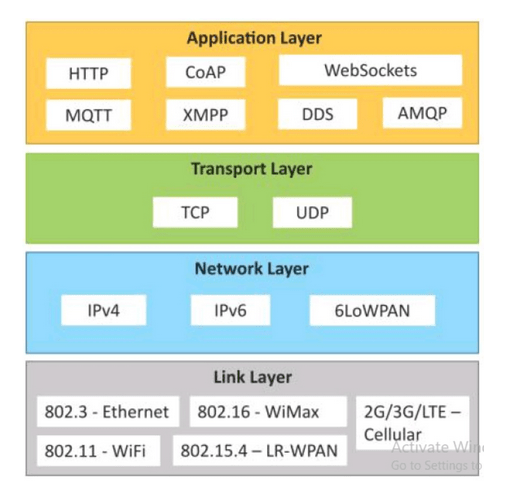
Figure 2: Protocols used in IoT, TCP/IP model, source: fb.com/IoTResearch
We can observe that in addition to the widely known HTTP protocol used, among other things, in web applications, there are also specific protocols such as CoAP, MQTT, XMPP, DDS, and AMQP. In the data link layer, specific protocols are found for different types of communication, such as Ethernet or WiFi, which can be used when the end device has access to the Internet via a cable or wireless connection. If this is not the case, cellular access or even WiMax remains an option.
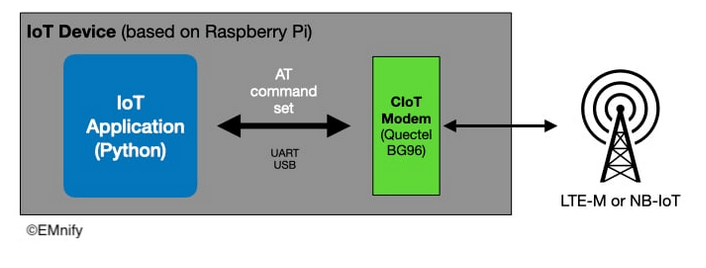
Figure 3: Diagram depicting IoT device communication with a cellular network, source: EMnify
Before diving into specific protocols, it’s worth discussing the general model of server-client communication and what a server actually is. A server can be any device operating on a network that offers certain services. In the context of IoT, a server typically refers to the same as a broker or a device with software that aggregates data from clients (IoT devices with sensors). The following communication models are distinguished in IoT:
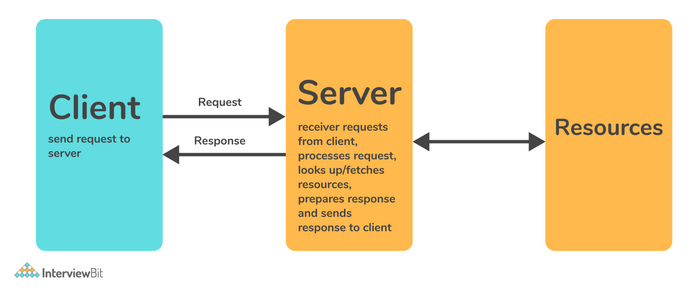
Figure 4: Request-response communication model, source: InterviewBit
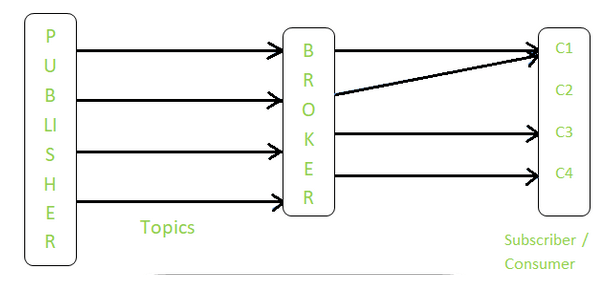
Figure 5: Publish-Subscribe communication model, source: geeksforgeeks.com
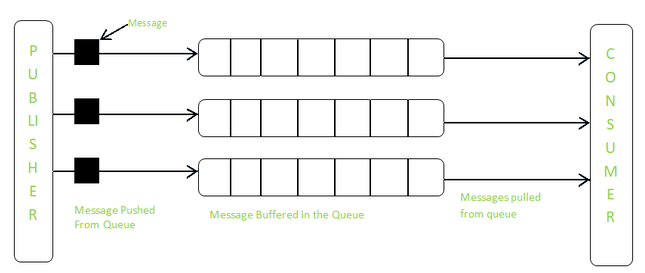
Figure 6: Push-pull communication model, source: geeksforgeeks.com

Figure 7: Exclusive Pair communication model, source: geeksforgeeks.com
As we can see from the examples above, the choice of a specific protocol in the application layer guides us toward a particular communication model. For instance, selecting MQTT leads to the use of the publish-subscribe model, HTTP corresponds to the client-server model, and WebSockets are associated with the Exclusive Pair model.
Due to the reduction in the cost of hardware components and technological advancements, including the development of artificial intelligence (we recommend our previous articles on this topic), sensors will soon be integrated into every aspect of the industry. If a company does not embrace modern solutions in its field, it may become less competitive in the market. Some of the key markets currently employing IoT solutions include:
Today, we’ve provided you with basic technical information about IoT systems, communication models, and real-world applications across various market sectors. We’ll continue the IoT topic next week, so if you’re interested, stay tuned!

10 Benefits of Custom Software for Your Business – Fewer Resources, Greater Efficiency
Dedicated software is an investment that increases company efficiency, minimizing IT resource consumption and supporting a sustainable development strategy.
Green IT

Responsible Software Development: How to Reduce Your Application’s Carbon Footprint?
Practical tips on how developers can actively reduce CO2 emissions by optimizing code, infrastructure, and application architecture.
Green ITInnovation

Green IT: How Technology Can Support Environmental Protection?
An introduction to the idea of Green IT – a strategy that combines technology with care for the planet.
Green ITInnovation