Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
 Author:
Author:Today we will delve into the more technical aspects of IoT devices and discuss application layer protocols in more detail. What technologies are available, which specific programming packages can be applied, and how do the various IoT-specific protocols differ from each other? All of this today. Welcome to our reading!
In our last article, we discussed the layered approach in computer networks and how the IoT system works at the network level. Today, we will start with what is most important for programmers from a networking perspective, which is the application layer and protocols such as MQTT and COAP.
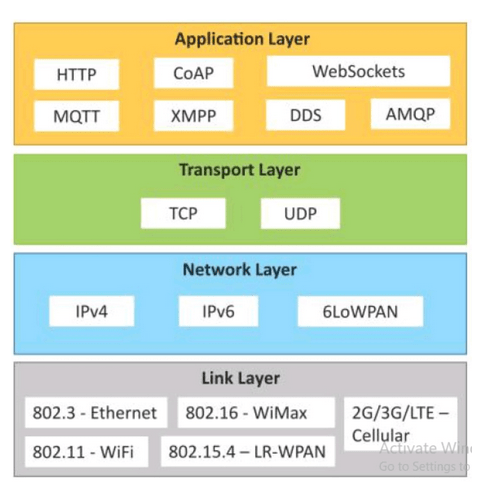
Figure 1: Protocols used in IoT, TCP/IP model, source: fb.com/IoTResearch
If we want to see the trends in IoT application protocols, we can use Google Trends, which indicates the most frequently searched technologies.
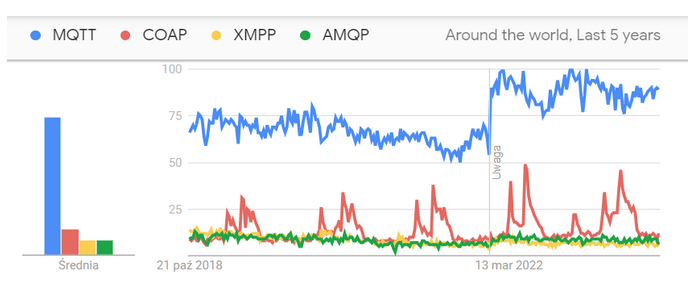
Figure 2 – Google Trends chart
https://trends.google.com/trends/explore?date=today%205-y&q=MQTT,COAP,XMPP,AMQP
It’s worth examining the trends for individual technologies, as there are some differences in interest distribution, especially in countries like China and the USA. However, globally, MQTT is the predominant solution, which we will try to present below.
MQTT (MQ Telemetry Transport) is a lightweight protocol that was created in 1999 and operates on a publish/subscribe model. It is used for message queuing and is a widely used solution in IoT devices. The MQTT standard defines two types of entities in the network: the client and the message broker. In 2012, one of the most popular open-source brokers, Mosquitto 1.0, was created. In 2013, the widely used cloud-based solution HiveMQ was created. In 2014, an update to the MQTT standard was released as version 3.1.1, and then in 2018, MQTT 5 was introduced.
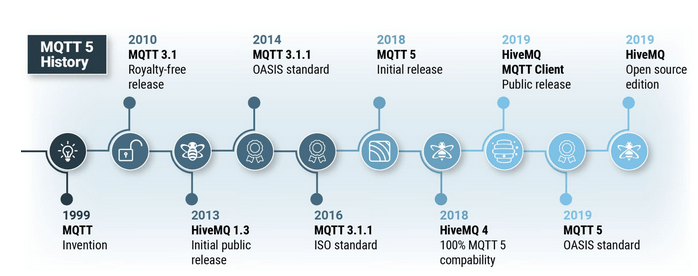
Figure 3 – MQTT history, source: hivemq.com
MQTT possesses several characteristics that both make it similar to and different from other application layer protocols like HTTP. Some of these characteristics include:
The connection between a client and a broker begins with the establishment of a TCP connection (if not using QUIC) and then the exchange of MQTT-specific packets.
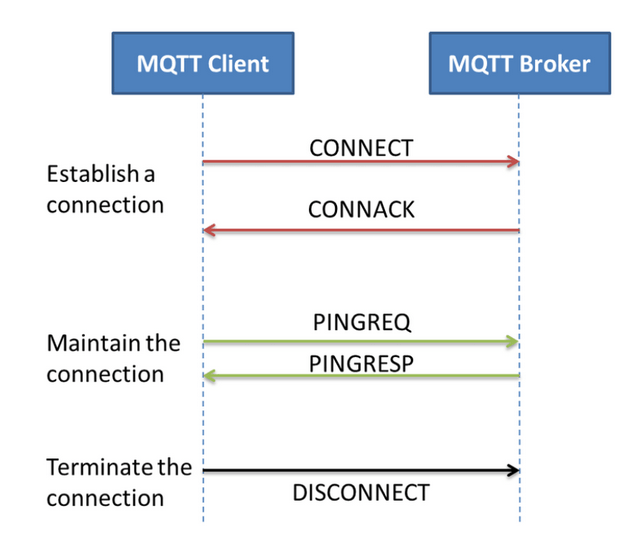
Figure 4 – MQTT packets used for managing the connection between a client and a broker, source: Ravi Kishore Kodali, researchgate.net
As seen in the above illustration, MQTT uses several types of messages for communication, which we will briefly describe:
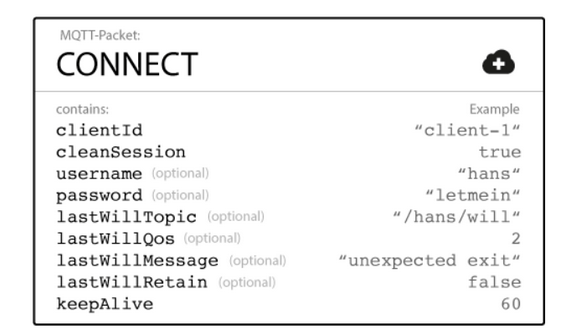
Figure 5: Contents of the CONNECT message, source: hivemq.com
Last Will Mechanism in MQTT allows the client to specify a message that the broker will publish on a specific topic in the event of an unexpected loss of the client’s connection. The client defines the topic on which the last will should be published and the content of the message. Parameters related to Last Will include:
There are also many other types of MQTT messages such as PUBACK, PUBREC, PUBREL, PUBCOMP, UNSUBSCRIBE, UNSUBACK.
We hope that today’s post was interesting, especially for technical people. We’ve touched on various aspects of technology related to both programming and computer networks. If you’re interested, we invite you to join us next week as we continue to explore the IoT topic.

Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
Green IT

Helm for the Second Time – Versioning and Rollbacks for Your Application
We describe how to perform an update and rollback in Helm, how to flexibly overwrite values, and discover what templates are and how they work.
AdministrationInnovation

Helm – How to Simplify Kubernetes Management?
It's worth knowing! What is Helm, how to use it, and how does it make using a Kubernetes cluster easier?
AdministrationInnovation