Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
 Author:
Author:Today we want to continue discussing topics related to IoT, or the Internet of Things. We’ll be talking about various other protocols that exist in the application layer and are associated with IoT systems. If you’re interested, we invite you to read on!
In 2023, the most popular protocol for IoT devices is MQTT, which we discussed in our last blog post. However, there are alternatives used in specific scenarios where MQTT cannot be applied.
The Constrained Application Protocol (CoAP) is a protocol designed to operate on hardware that is inherently limited, such as due to small memory or computational resources. It is recommended for devices running on batteries due to its efficient use of energy resources. The CoAP standard (RFC 7252) was established in 2014, making it a relatively new solution compared to MQTT (1999). CoAP is suitable for larger-scale IoT projects and devices with limited power resources. It has several characteristic features in terms of technical aspects, including:
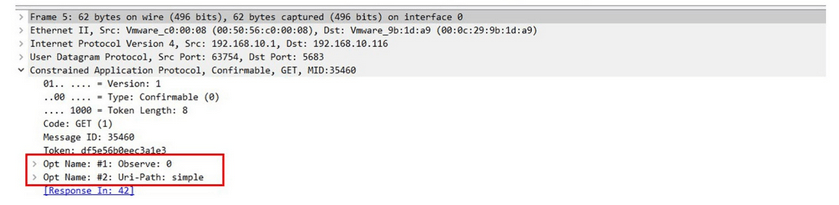
Figure 1: CoAP datagram in Wireshark, showing the Observe flag, source: journals.sagepub.com
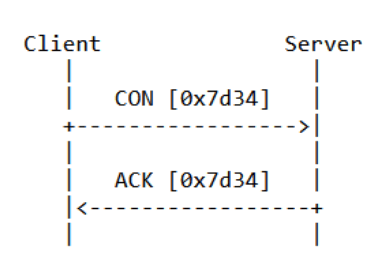
Figure 2: Example of communication confirmation from client to server in CoAP, source: RFC7252
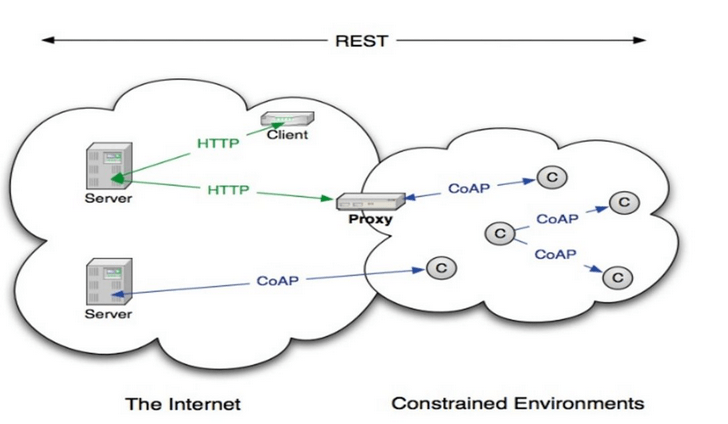
Figure 3 – Transition between HTTP and CoAP using a proxy, source: e2e.ti.com
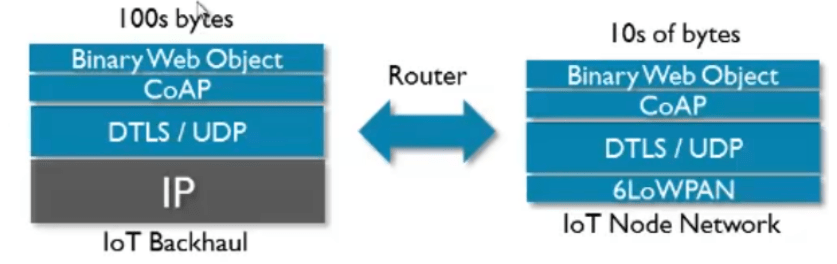
Figure 4 – Possible network stack for an IoT device using CoAP, source: ARM Youtube
6LoWPAN is a protocol below the transport layer that allows the use of IPv6 in low-power wireless networks. When combined with CoAP (the application layer), it enables efficient communication for IoT devices. This is achieved by adapting IPv6 packets to the constraints of such networks, using IPv6 addresses, header compression, fragmentation, and enabling the creation of mesh networks. CoAP, as a lightweight protocol, fits perfectly into 6LoWPAN, allowing access and resource management in resource-constrained environments.
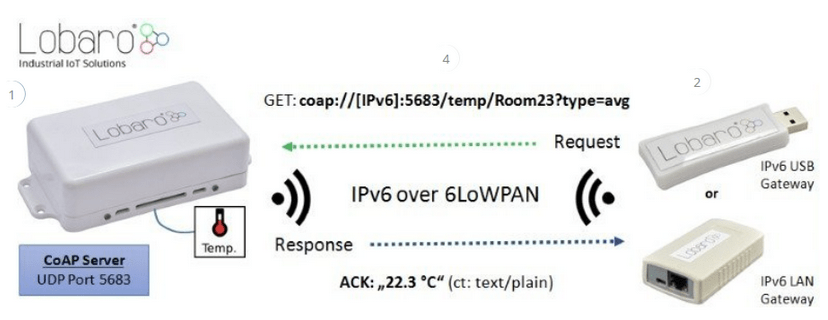
Figure 5 – Communication scheme between devices using COAP and 6LoWPAN, source: lobaro.com
CoAP offers many more functionalities that we cannot cover here. However, we hope this short article will provide you with a better understanding of the IoT topic as a whole.
Today we have introduced you to an alternative to MQTT – a CoAP protocol similar to HTTP, efficient on limited resources, secure with DTLS. We also encourage you to take a look at the sources. See you next week with a new topic!

Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
Green IT

Helm for the Second Time – Versioning and Rollbacks for Your Application
We describe how to perform an update and rollback in Helm, how to flexibly overwrite values, and discover what templates are and how they work.
AdministrationInnovation

Helm – How to Simplify Kubernetes Management?
It's worth knowing! What is Helm, how to use it, and how does it make using a Kubernetes cluster easier?
AdministrationInnovation