10 Benefits of Custom Software for Your Business – Fewer Resources, Greater Efficiency
Dedicated software is an investment that increases company efficiency, minimizing IT resource consumption and supporting a sustainable development strategy.
 Author:
Author:Hey, today as Innokrea we continue the topic of Masscan, its specifics and advanced options (see part 1 abour scanning of Internet here). We will also explain what a reflection attack is and show it with a specific example. If you want to know more, we encourage you to read on!
File formats
The output we collect from scans can be saved in many convenient formats for processing, such as XML, JSON. We do this using a dedicated switch or command –output-format <format> and –output-filename <filename>.
For example: masscan –output-format xml –output-filename output.xml
There are also dedicated parameters for formats that are a combination of the two commands mentioned above.
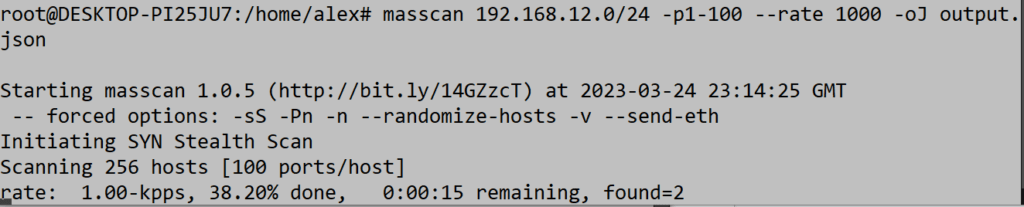
Figure 1: Scanning a local network to a JSON file.
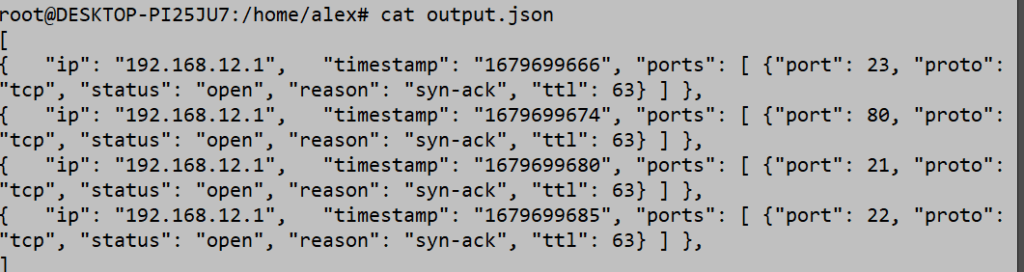
Figure 2: Contents of the output.json file.
Additional Masscan options
It’s worth mentioning some other interesting Masscan parameters that can be used while working with this tool.
–echo – instead of executing a scan, save the current parameter configuration to disk
-c <filename> – load configuration from a file
-e <iface> – specify the interface through which traffic should flow. If not specified, Masscan will choose the one with the default gateway set
–exclude <range> – exclude a specified range from scanning
–excludefile <filename> – exclude addresses specified in a file from scanning
–retries <number> – how many times the scanner should retry a request. Because it is stateless, it will retry regardless of whether it received a response
–pcap <filename> – export to pcap format
–pfring – use the pfring driver. It must be installed beforehand.
–-nmap-payloads – scan using scanning methods from NMAP software.
–resume <filename> – if the user presses Ctrl-C, Masscan will stop and create a paused.conf file. Then it can be restarted by specifying this parameter
–wait <seconds> – how many seconds Masscan should wait for a response after sending a request (default is 10s)
More options can be found in the manual on the website https://manpages.org/masscan/8
Increasing speed through instance usage
The flexibility of using parameters and adjusting them to the working instance of the system is important. Due to the number of parameters, it is possible to customize a scan to one’s needs and speed it up to speeds that, for example, NMAP is not capable of. For this purpose, instance multiplication can also be used, as Masscan offers so-called sharding. It is responsible for dividing the given range of addresses between Masscan instances in order to scan in parallel. The output should be written to separate files because it is not possible to write to a single file from multiple Masscan instances. To do this, two terminal instances should be started, and the same seed (initial number of the random number generator) should be used:
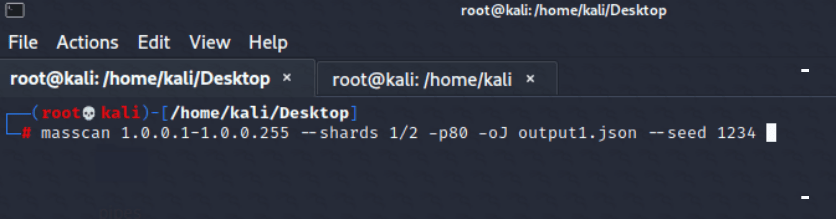
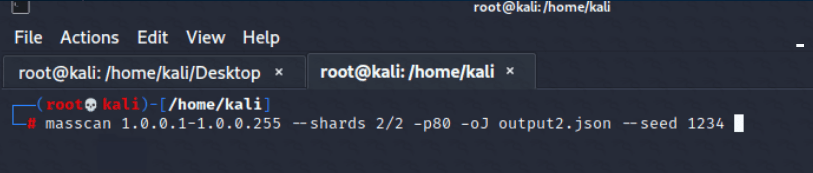
Figure 3 & 4: Using sharding to divide the scan between two Masscan instances
The output is saved to two separate files, and each record, thanks to the use of the same seed, is different even between the outpu1.json and output2.json files.
Reflection attack scenario
Since the –adapter-ip parameter and a separate TCP/IP protocol stack can be used to set any source IP address, a public address of any server that we want to take off the network can be provided. Then, we send a request to a certain other service, and the service sends a response to the server indicated in the source address. If we use an amplification attack, i.e., amplification consisting of receiving a large response clogging the connection when sending a small amount of data, we can deprive someone of access to the network at a low cost.
To prevent this, an ISP can use so-called “egress filtering”. Then, the router on the ISP side can check whether the source address in a given packet matches the local subnet from which the packet came. If not, it can block traffic. This can be checked by sending a spoofed message to our own server on which we are listening on a public address. It should also be remembered that if a particular provider does not allow scanning of their infrastructure in their regulations, it should not be done, or one should be prepared for the consequences.
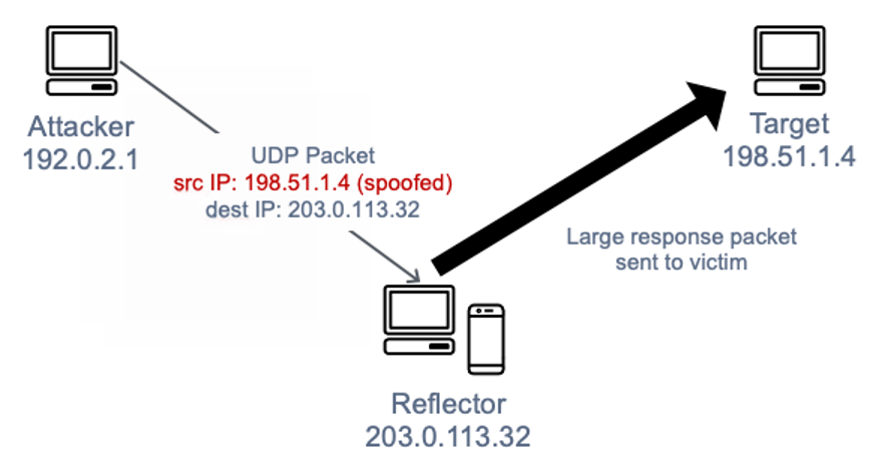
Figure 5: Reflection attack. Source: docs.aws.amazon.com.
Memcached – a real attack example
Memcached is a caching system used to optimize the performance of web applications. It stores query results, for example. Memcached services should not be exposed to the public, but in 2018, some of them were partially exposed. There were no authentication mechanisms, as only the web application exposed to the world should be able to communicate with Memcached.
Attack procedure:
1.The attacker scans for exposed Memcached services.
2.Having a list of such servers, the attacker can change their configuration and fill buffers with a large amount of data.
3.The attacker then sends a GET request for that data using a spoofed source address.
4.The content of the buffer, which is many times larger than the GET request, is sent to our target as a UDP stream.
This is how in 2018 GitHub servers were attacked, which were overloaded with traffic of 1.35Tb/s. This is 1350Gb/s or 170GB/s.
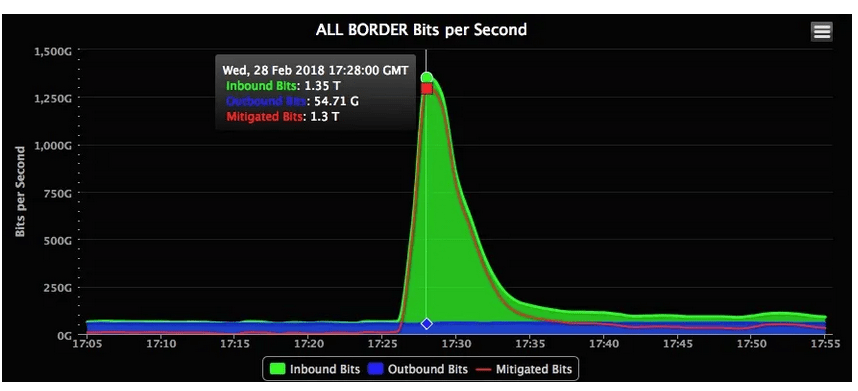
Figure 6: Graph of incoming data during the attack on GitHub. Source: Akamai/Wired.
This is a reflection + amplification attack, as we bounce off the Memcached server by spoofing IP and sending a small request, we can receive a very large response. This allows attackers with limited resources to launch a large-scale DDoS attack on a major Internet service.
Summary
We hope we have provided some insight into the topic of mass scanning on the Internet. Masscan can be used to gather data on a massive scale and draw global conclusions, such as how many devices may be vulnerable to a particular attack. Banner analysis can lead us to discover services running on a server. It is also worth noting that such a scan does not provide detailed information, such as NMAP software.
Sources:

10 Benefits of Custom Software for Your Business – Fewer Resources, Greater Efficiency
Dedicated software is an investment that increases company efficiency, minimizing IT resource consumption and supporting a sustainable development strategy.
Green IT

Responsible Software Development: How to Reduce Your Application’s Carbon Footprint?
Practical tips on how developers can actively reduce CO2 emissions by optimizing code, infrastructure, and application architecture.
Green ITInnovation

Green IT: How Technology Can Support Environmental Protection?
An introduction to the idea of Green IT – a strategy that combines technology with care for the planet.
Green ITInnovation