Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
 Author:
Author:The implementation of modern IT technologies is based on various needs, often related to the need to take on various challenges or overcome obstacles. This is the case when a company acts as a potential or actual buyer and user of a new IT technology, and it is also the case when, as the creator and owner of a new solution, the company tries to find customers ready to purchase it. In any case, in the overall process of IT technology transfer, the following three main phases can be distinguished (Fig. 1):
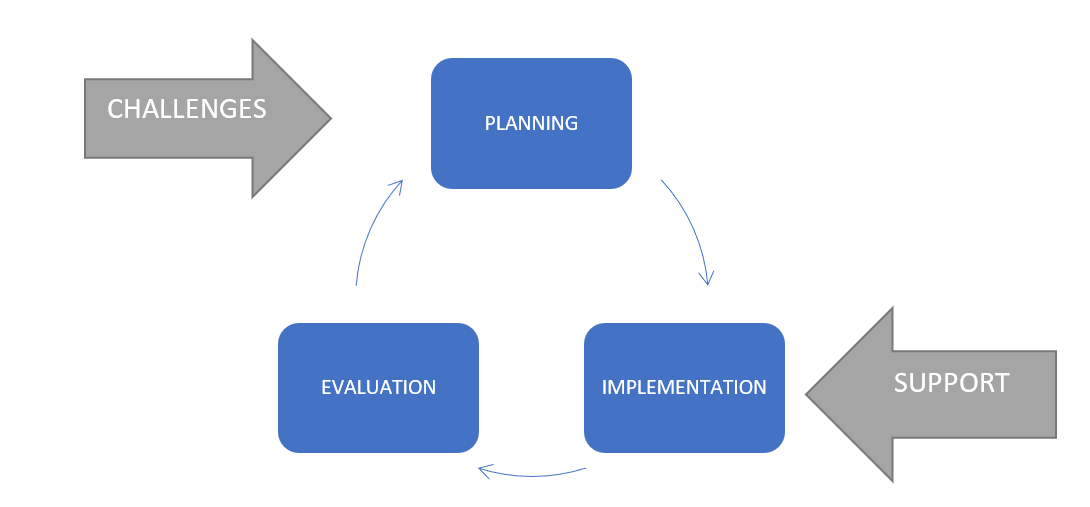
Figure 1. The general process of IT technology transfer in the company
Source: Author’s own elaboration.
Under certain conditions, the overall process of IT technology transfer in a company takes on more detailed forms. From the point of view of the enterprise, we can distinguish (on the basis of P. Głodek and M. Gołębiowski) the framework process of technology transfer (Fig. 2):
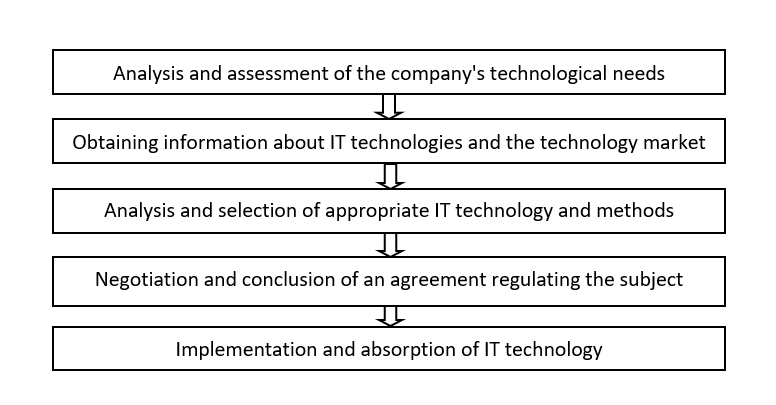
Figure 2. The framework process of IT technology transfer from the point of view of an enterprise, according to P. Głodek and M. Gołębiowski
Based on: P. Głodek, M. Gołębiowski, Technology transfer in small and medium-sized enterprises, PARP, Warsaw 2006, p. 14.
Commenting on the discussed approach to the framework process of IT technology transfer, it can be stated that:
A different approach to technology transfer was adopted by a team led by K. Santarek (Characteristic. 3). According to him, the technology transfer process includes[1]:
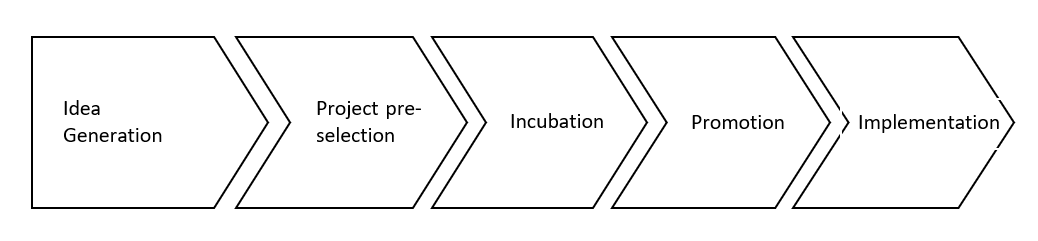
Figure 3. The process of technology transfer according to the team edited by K. Santarek
Source: K. Santarek (ed.), Technology transfer from academia to business. Creating Technology Transfer Mechanisms, PARP, Warsaw, September 2008, p. 87.
Such a way of approaching the process of IT technology transfer seems to correspond more to the situation of handing over one’s own technologies to other recipients and users, in accordance with the logic of sales. This is contrary to the approach to the framework process of technology transfer by P. Głodek and M. Gołębiowski, directed in accordance with the logic of purchase.In both approaches, there is a phase of implementation of solutions, but in the framework process of technology transfer, according to the above-mentioned authors, it is the implementation in the company’s own enterprise, in the transfer process according to K. Santark’s team – in the enterprise of the technology buyer. Despite the differences in the starting points and goals of the technology transfer process, there are a number of common regularities in both approaches, which are discussed further in this article.
Taking into account the situation and R&D potential of small and medium-sized enterprises, it can be concluded that they are much more often interested in purchasing technology. This does not mean that there are no innovative SMEs offering their own technologies to interested buyers. However, this is a less common situation. In order to maintain the universality of the study, in specific situations the issue of transfer in cases where its initiator and organizer is a company selling technology has also been highlighted.
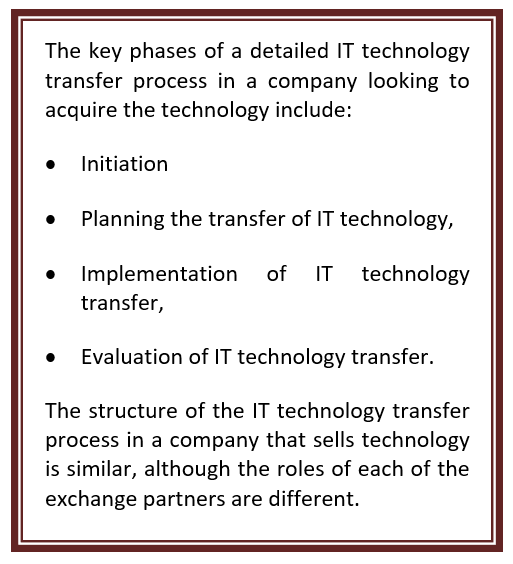
Based on the general model of technology transfer (Fig. 2), the following are detailed process of IT technology transfer in the company (Fig. 4). His The key phases are as follows.
All activities covered by a detailed process of IT technology transfer in the company are closed by a feedback loop, ensuring the improvement of the adopted solutions, in accordance with changes in the company itself and in its environment.
The process of transferring IT technology in a company that makes technology available to another external user is slightly different.
In the initiation phase, the analysis of the company’s environment is focused on searching for potential segments and groups of customers who may be interested in the offered IT technology.
After defining them, in the planning phase of IT technology transfer, the company undertakes contacts and talks with organizations – candidates for users of the offered technology, striving to negotiate the best possible contract terms.
The implementation and evaluation of the transfer of IT technology is carried out in a manner similar to the one discussed above, taking into account the distinctiveness (or rather the roles of each of the exchange partners).
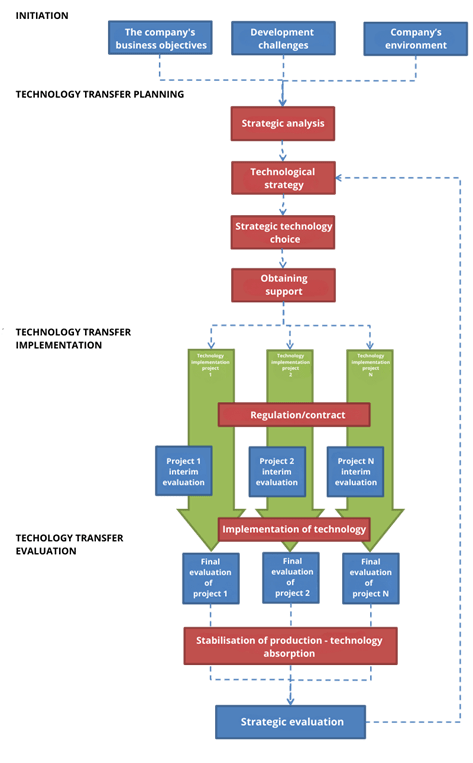
Figure 4. Detailed process of IT technology transfer in the company
Source: Author’s own elaboration.
[1] K. Santarek (ed.), Transfer of technology from academia to business. Creating Technology Transfer Mechanisms, PARP, Warsaw, September 2008, p. 87.

Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
Green IT

Helm for the Second Time – Versioning and Rollbacks for Your Application
We describe how to perform an update and rollback in Helm, how to flexibly overwrite values, and discover what templates are and how they work.
AdministrationInnovation

Helm – How to Simplify Kubernetes Management?
It's worth knowing! What is Helm, how to use it, and how does it make using a Kubernetes cluster easier?
AdministrationInnovation