Responsible Software Development: How to Reduce Your Application’s Carbon Footprint?
Practical tips on how developers can actively reduce CO2 emissions by optimizing code, infrastructure, and application architecture.
 Author:
Author:Already at the planning stage of an IT project, it is necessary to define what is to be included in its scope and estimate the schedule and budget. The link between scope, budget, and schedule is often referred to as “The Triple Constraint Triangle” because they are inextricably linked. Many entrepreneurs have certainly had the opportunity to experience dilemmas, for example, when ordering new software for a company, they wanted to obtain it “quickly, cheaply and in good quality”. In such a situation, they often encountered the contractor’s response that he could only meet some of these requirements, for example:
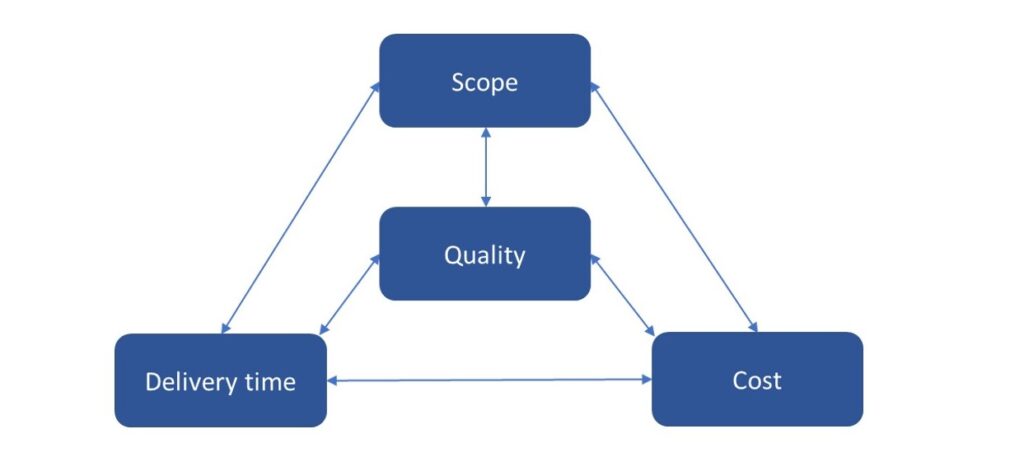
Dependencies between scope, budget, schedule and quality also occur during project implementation. If at any time it is found that the scope of work under the project should be increased, it will inevitably be associated with an extension of its implementation time (schedule) and / or an increase in costs (budget).
The above description of selected project features is the basic starting point for the implementation of an IT project. Of course, each project is by definition unique and has a number of conditions that each entrepreneur must consider separately and properly take into account. However, after carrying out thorough preparatory, descriptive and planning work at the beginning, when everyone agrees as to the intended goals and effects, and the budget, scope and schedule are realistic, the chances for the success of the project increase significantly.
There are many computer programs and techniques that do not require a computer but focus on the activities of a small team in one place for budget planning and scheduling. It is worth getting acquainted with such tools as the Gantt chart, PERT analysis, milestones, network charts, as well as other useful methods of project planning.
A well done planning of an IT project will most likely allow us to avoid many implementation problems in the future. Here, too, the Pareto principle works: 20% of the effort (devoted to planning and selecting the right partner) will be responsible for at least 80% of the effects of the IT project. Mistakes made at the stage of planning an IT project can cost the company a lot (or in extreme cases be “irreparable”), especially when it comes to a dedicated software.

Responsible Software Development: How to Reduce Your Application’s Carbon Footprint?
Practical tips on how developers can actively reduce CO2 emissions by optimizing code, infrastructure, and application architecture.
Green ITInnovation

Green IT: How Technology Can Support Environmental Protection?
An introduction to the idea of Green IT – a strategy that combines technology with care for the planet.
Green ITInnovation

CI/CD + Terraform – How to Deploy Your Application on AWS? – Part 2
Learn about the possibilities of GitHub Actions - how to quickly deploy an application using GitHub Actions using AWS and Terraform technologies.
AdministrationProgramming