Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
 Author:
Author:IT technologies, like other technologies and products of human thought and work, in different periods of their existence have different meanings and value for their users. Under the influence of various activities to which a given IT technology is subject (i.e. changes, extensions, improvements, changing expectations, user experiences), its potential changes over time. This phenomenon is illustrated by the technology life cycle “s-curves” as shown below in Figure 1.
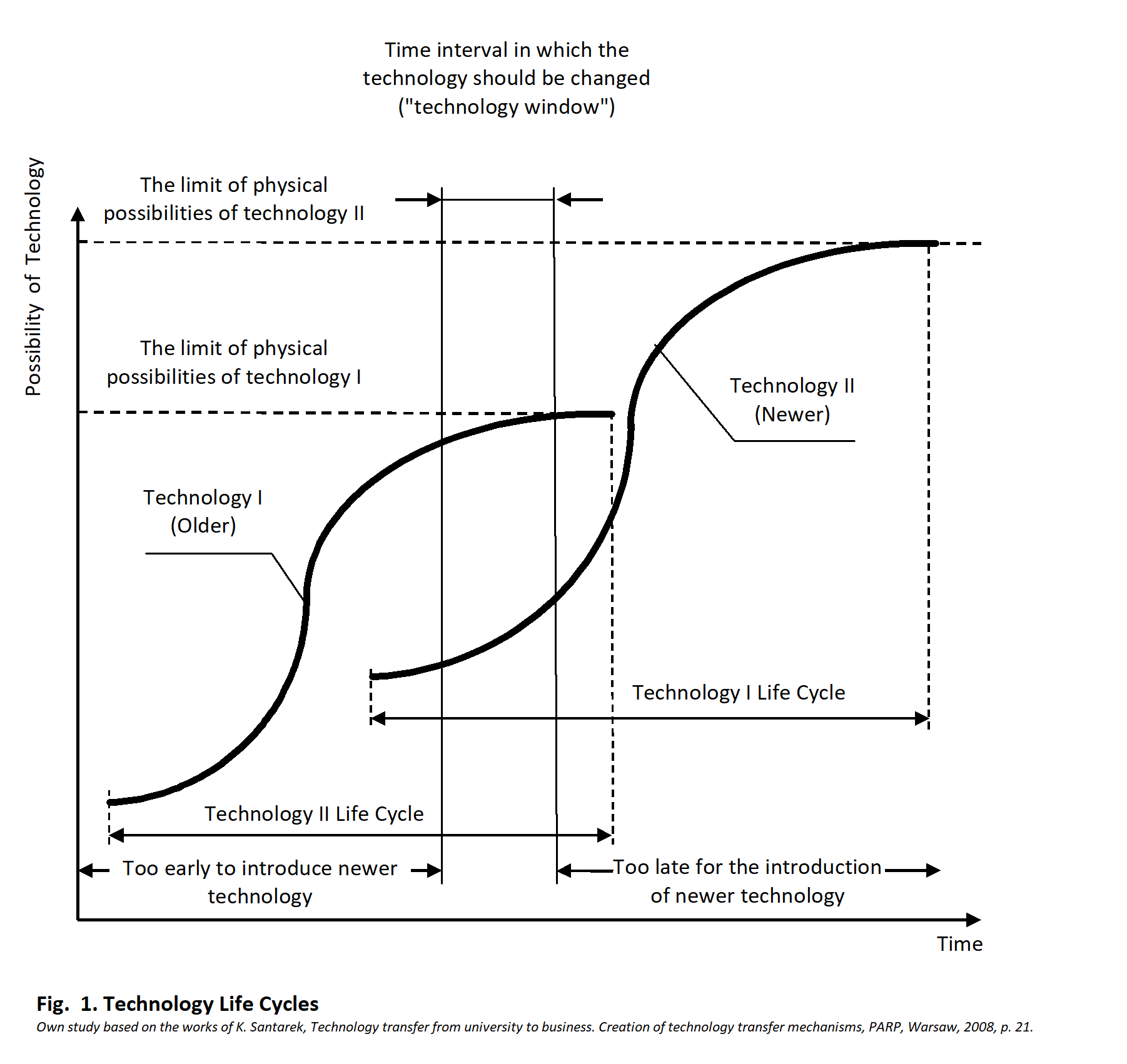
Quite often, in the early stages of their life cycle, newer IT technologies fail to achieve the parameters and capabilities of older generation technologies. For a new technology to fully realize its potential, it needs to be refined, which generally requires a lot of analysis, research and improvement. This overlaps with the process of emergence and development of new technologies, which often uses new ideas and methods of operation, with higher parameters and possibilities. They replace older technologies in industrial applications, providing new opportunities for their users.
There are at least two basic decision challenges related to the technology life cycle and the introduction of new generation IT technologies, including:
Withdrawal from an older technology too early risks losing the benefits of using it in the period when it meets the expectations related to it. And when the withdrawal occurs before any return on investment is realized may even result in some kind of loss to the business. Furthermore, if it’s too late to start work on implementing a new technology, it may no longer be possible to catch up to your competitors if they have already undertaken the appropriate work in a timely manner, resulting in loss of competitive advantage or even the ability to compete in general. Hence the importance and the need to carefully prepare decisions to undertake work on introducing new technologies.
Taking into account the importance and competitive power of technology and its potential impact on companies that enjoy a market leading position due to having some technological advantage, technologies used in specific industries or sectors can be classified as follows (after G. Stonehouse):
A company interested in gaining a competitive advantage on the market should primarily use key technologies, with the option of replacing them in the future with technologies that set the pace (progressive). Using commonly used base technologies to gain an advantage is usually not enough.
The typology of technology, with the degree of saturation of potential applications and decisions about their future in the company, is presented in Figure 2.
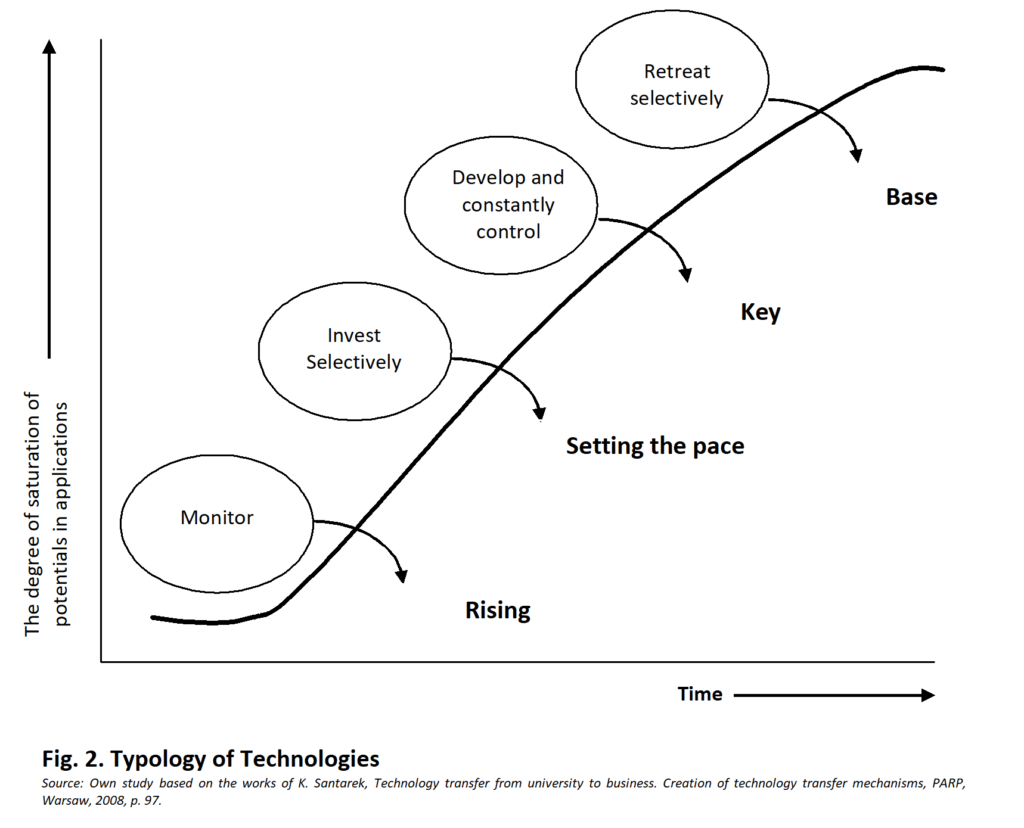
Base technologies achieve the highest degree of saturation of potential applications. These applications, however, reach a limit (or maximum level of efficiency), which will decrease in the future, because market players, striving to gain or maintain a competitive advantage, will increasingly introduce key technologies. Hence the recommendation for base technologies is to withdraw or “retreat selectively”.
Recommendations for other types of technology are:
Here at INNOKREA, we also had to deal with aging technologies. Around 4 years ago, we developed an e-commerce solution called internalBID. The solution enables companies to sell off any retired equipment through a dedicated auction system.
The original MVP (Minimum Viable Product) was developed based on WordPress, however, we realised through our testing that there were some limitations with its customization. It was obvious that we needed to move to a different technology.
To ensure that our solution is future-proof and meets customer expectations, we made the decision to re-develop the solution by rewriting it in the latest software technologies.
We are constantly monitoring the market and looking for opportunities on where we need to improve our solution. Such decisions help drive our business forward and give us a competitive edge, but most importantly, it ensures our viability by keeping up with the changes in technologies.
So in conclusion, the market position of a company using certain technologies depends not only on the degree of novelty and competitive strength of the technology, but also on the degree of how it masters the technology and absorbs it into the business to derive value.

Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
Green IT

Helm for the Second Time – Versioning and Rollbacks for Your Application
We describe how to perform an update and rollback in Helm, how to flexibly overwrite values, and discover what templates are and how they work.
AdministrationInnovation

Helm – How to Simplify Kubernetes Management?
It's worth knowing! What is Helm, how to use it, and how does it make using a Kubernetes cluster easier?
AdministrationInnovation